How to Configure Let’s Encrypt SSL in Lighttpd Server

Nowadays, HTTPS sites are every where and they are considered very secure and trusted. After the launch of Let’s Encrypt CA, there is a tremendous increase of HTTPS sites on the internet.
Fyi, Let’s Encrypt CA is a certificate authority that provides free x.509 certificate for web servers and control panel.
Here, we will create a Free Let’s Encrypt certificate for your Lighttpd server so that your website will be one of the secured website available online.
Install Certbot
Certbot is available on EPEL repository, so configure EPEL repository on CentOS 7 / RHEL 7. For Ubuntu, Certbot PPA should be configured.
### CentOS 7 / RHEL 7 ### rpm -ivh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm ### Ubuntu / Debian ### apt-get update apt-get install software-properties-common add-apt-repository ppa:certbot/certbot apt-get update
Now, use yum in CentOS and apt-get in Debian/Ubuntu to install the certbot client.
### CentOS 7 / RHEL 7 ### yum install certbot ### Ubuntu 16.04 / Debian 9 ### apt-get install certbot ### Debian 8 ### apt-get install certbot -t jessie-backports
Install and Start the Lighttpd
Follow our earlier article on the installation of Lighttpd server CentOS 7 / Debian 9 / Ubuntu 16.04.
READ: How to install Lighttpd on CentOS 7 / RHEL 7
READ: How to install Lighttpd on Debian 9 / Ubuntu 16.04
Make sure the Lighttpd service is up and running.
service lighttpd status
Output:
● lighttpd.service - Lighttpd Daemon Loaded: loaded (/lib/systemd/system/lighttpd.service; enabled; vendor preset: enabled) Active: active (running) since Wed 2017-08-09 02:20:29 UTC; 27min ago Process: 5656 ExecStartPre=/usr/sbin/lighttpd -t -f /etc/lighttpd/lighttpd.conf (code=exited, status=0/SUCCESS) Main PID: 5676 (lighttpd) Tasks: 1 Memory: 2.1M CPU: 277ms CGroup: /system.slice/lighttpd.service └─5676 /usr/sbin/lighttpd -D -f /etc/lighttpd/lighttpd.conf Aug 09 02:20:29 web2 systemd[1]: Stopped Lighttpd Daemon. Aug 09 02:20:29 web2 systemd[1]: Starting Lighttpd Daemon... Aug 09 02:20:29 web2 lighttpd[5656]: Syntax OK Aug 09 02:20:29 web2 systemd[1]: Started Lighttpd Daemon.
Create a certificate for your domain
During the certification creation, certbot creates .well-known/acme-challenge directory inside the document root of your web server. Then, Let’s Encryption validation server makes HTTP requests to that directory and validates whether the DNS is correctly pointing to the server running certbot or not.
So, ensure you have correctly set up a virtual host for your custom domain and is accessible over the internet.
READ: How to setup virtual hosts in Lighttpd server
Use the following command to create a Let’s Encrypt certificate.
certbot certonly --webroot -w /srv/htdocs/web.itzgeek.com -d web.itzgeek.com
-w : Path of your document root.
-d : Fully Qualified Domain Name
Follow the interactive prompt and generate the required certificate.
Saving debug log to /var/log/letsencrypt/letsencrypt.log Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel):[email protected] Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org ------------------------------------------------------------------------------- Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.1.1-August-1-2016.pdf. You must agree in order to register with the ACME server at https://acme-v01.api.letsencrypt.org/directory ------------------------------------------------------------------------------- (A)gree/(C)ancel: A ------------------------------------------------------------------------------- Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about EFF and our work to encrypt the web, protect its users and defend digital rights. ------------------------------------------------------------------------------- (Y)es/(N)o: N Obtaining a new certificate Performing the following challenges: http-01 challenge for web.itzgeek.com Using the webroot path /srv/htdocs/web.itzgeek.com for all unmatched domains. Waiting for verification... Cleaning up challenges IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at /etc/letsencrypt/live/web.itzgeek.com/fullchain.pem. Your cert will expire on 2017-11-06. To obtain a new or tweaked version of this certificate in the future, simply run certbot again. To non-interactively renew *all* of your certificates, run "certbot renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
Combine both certificate and private key in one file.
cat /etc/letsencrypt/live/web.itzgeek.com/cert.pem /etc/letsencrypt/live/web.itzgeek.com/privkey.pem > /etc/letsencrypt/live/web.itzgeek.com/web.pem
Update Lighttpd configuration
Update your Lighttpd server configuration to use the created certificate.
vi /etc/lighttpd/lighttpd.conf
Use the below information.
$SERVER["socket"] == ":443" {
ssl.engine = "enable"
ssl.pemfile = "/etc/letsencrypt/live/web.itzgeek.com/web.pem" # Combined Certificate
ssl.ca-file = "/etc/letsencrypt/live/web.itzgeek.com/chain.pem" # Root CA
server.name = "web.itzgeek.com" # Domain Name OR Virtual Host Name
server.document-root = "/srv/htdocs/web.itzgeek.com" # Document Root
server.errorlog = "/var/log/lighttpd/web.itzgeek.com_error.log"
accesslog.filename = "/var/log/lighttpd/web.itzgeek.com_access.log"
}
Restart Lighttpd service.
service lighttpd restart
Redirect HTTP requests to HTTPS – Lighttpd
We can also configure HTTP to HTTPS redirection on Lighttpd server so that the traffic comes to non-HTTPS site redirect to the HTTPS site.
Update /etc/lighttpd/lighttpd.conf with the below information.
$HTTP["scheme"] == "http" {
$HTTP["host"] == "web.itzgeek.com" { # HTTP URL
url.redirect = ("/.*" => "https://web.itzgeek.com$0") # Redirection HTTPS URL
}
}
Verify the HTTPS
Place an index.html on document root of the virtual host.
echo "Testing SSL" > /srv/htdocs/web.itzgeek.com/index.html
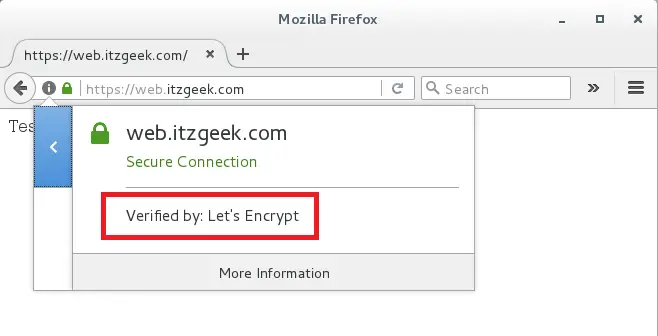
Verify the Let’s Encrypt certificate by visiting HTTPS version of your website.
OR
You should get HTTPS version of your site now.
Certificate Renewal:
Let’s Encrypt certificates comes with a validity of 90 days; it is highly advisable to configure the cron (Linux Scheduler) job to renew your certificates before they expire.
Before you configure the cron job, run the below command to simulate automatic renewal of your certificate.
certbot renew --dry-run
Output:
Saving debug log to /var/log/letsencrypt/letsencrypt.log ------------------------------------------------------------------------------- Processing /etc/letsencrypt/renewal/web.itzgeek.com.conf ------------------------------------------------------------------------------- Cert not due for renewal, but simulating renewal for dry run Starting new HTTPS connection (1): acme-staging.api.letsencrypt.org Renewing an existing certificate Performing the following challenges: http-01 challenge for web.itzgeek.com Waiting for verification... Cleaning up challenges ------------------------------------------------------------------------------- new certificate deployed without reload, fullchain is /etc/letsencrypt/live/web.itzgeek.com/fullchain.pem ------------------------------------------------------------------------------- ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates below have not been saved.) Congratulations, all renewals succeeded. The following certs have been renewed: /etc/letsencrypt/live/web.itzgeek.com/fullchain.pem (success) ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates above have not been saved.)
If that appears to be working properly, configure a cron job for the below command.
certbot renew
After you renew your certificate, do not forget to combine both certificate and private key in one file.
That’s All.
