Setup Let’s Encrypt With Apache on CentOS 7 & 6 / RHEL 7 & 6 / Debian 9 / Ubuntu 16.04
Let’s Encrypt is a widely know certificate authority that provides free X.509 SSL certificates for TLS encryption, launched in April 2016.
It is an automated process to eliminate the current complex process of certificate creation, validation, signing, implementation, and renewal of certificates for secure websites. To generate a certificate for any domain, you should have terminal/shell access and Certbot ACME client to be installed. It automates certificate issuance and installation with no downtime.
At the time of writing, only Apache, Nginx, Haproxy, and Plex are supported for the automated process. From my experience. I suggest you not to go through the automated process as it may mess up your web server configuration sometime if you are not properly answered questions it asks during the process.
The manual process is also very simple, steps as follows.
1. Create a certificate for your domain.
2. Update web server configuration to use the created certificate.
Prerequisites
Assuming that you have LAMP stack configured on CentOS / Debian / Ubuntu.
READ: How to Install LAMP Stack on CentOS 7 / RHEL 7
READ: How to Install LAMP Stack on Debian 9
READ: How to Install LAMP Stack on Ubuntu 16.04 / Ubuntu 14.04
Install Let’s Encrypt
Login as the root user or switch to the root user.
su -
OR
sudo su -
Certbot is available on EPEL repository for CentOS, and Certbot PPA should be configured on Ubuntu.
### CentOS 7 ### rpm -ivh https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm ### CentOS 6 ### https://dl.fedoraproject.org/pub/epel/epel-release-latest-6.noarch.rpm ### RHEL 7 ### subscription-manager repos --enable rhel-7-server-optional-rpms ### RHEL 6 ### subscription-manager repos --enable rhel-6-server-optional-rpms ### Ubuntu ### apt-get update apt-get install -y software-properties-common add-apt-repository ppa:certbot/certbot
Now, use the following command to install the certbot client.
### CentOS / RHEL ### yum install -y certbot ### Ubuntu 16.04 / Debian 9 ### apt-get update apt-get install -y certbot ### Debian 8 ### apt-get install -y certbot -t jessie-backports
Install and Start the Web Server.
### CentOS / RHEL ### yum -y install httpd mod_ssl service httpd start ### Ubuntu / Debian ### apt-get install -y apache2
Verify the web service by going to the following URL.
You should get the default Apache web page.
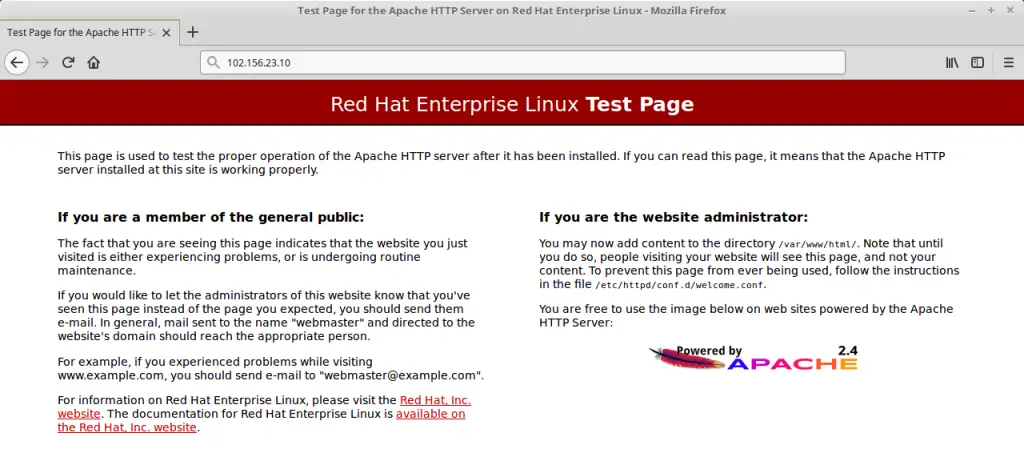
Create a certificate for your domain
Use the certbot command to create a Let’s Encrypt certificate manually.
certbot certonly --webroot -w /var/www/html -d web.itzgeek.com
-w: Path of your document root.
-d: FQDN
Follow the interactive prompt and generate the required certificate.
Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator webroot, Installer None Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): [email protected] Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org ------------------------------------------------------------------------------- Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v01.api.letsencrypt.org/directory ------------------------------------------------------------------------------- (A)gree/(C)ancel: A ------------------------------------------------------------------------------- Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about EFF and our work to encrypt the web, protect its users and defend digital rights. ------------------------------------------------------------------------------- (Y)es/(N)o: N Obtaining a new certificate Performing the following challenges: http-01 challenge for web.itzgeek.com Using the webroot path /var/www/html for all unmatched domains. Waiting for verification... Cleaning up challenges IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/web.itzgeek.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/web.itzgeek.com/privkey.pem Your cert will expire on 2018-05-14. To obtain a new or tweaked version of this certificate in the future, simply run certbot again. To non-interactively renew *all* of your certificates, run "certbot renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
Update web server configuration
Update the apache server configuration to use the created certificate.
CentOS / RHEL:
Edit the configuration file.
vi /etc/httpd/conf.d/ssl.conf
Update the below information.
Listen 443 https SSLPassPhraseDialog exec:/usr/libexec/httpd-ssl-pass-dialog SSLSessionCache shmcb:/run/httpd/sslcache(512000) SSLSessionCacheTimeout 300 SSLRandomSeed startup file:/dev/urandom 256 SSLRandomSeed connect builtin SSLCryptoDevice builtin <VirtualHost _default_:443> DocumentRoot "/var/www/html" ServerName web.itzgeek.com:443 ErrorLog logs/ssl_error_log TransferLog logs/ssl_access_log LogLevel warn SSLEngine on SSLProtocol all -SSLv2 -SSLv3 SSLCipherSuite ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS SSLHonorCipherOrder on SSLOptions +StrictRequire SSLCertificateFile /etc/letsencrypt/live/web.itzgeek.com/cert.pem SSLCertificateKeyFile /etc/letsencrypt/live/web.itzgeek.com/privkey.pem SSLCertificateChainFile /etc/letsencrypt/live/web.itzgeek.com/chain.pem <Files ~ "\.(cgi|shtml|phtml|php3?)$"> SSLOptions +StdEnvVars </Files> <Directory "/var/www/cgi-bin"> SSLOptions +StdEnvVars </Directory> BrowserMatch "MSIE [2-5]" \ nokeepalive ssl-unclean-shutdown \ downgrade-1.0 force-response-1.0 CustomLog logs/ssl_request_log \ "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b" </VirtualHost>
Ubuntu / Debian:
nano /etc/apache2/sites-available/default-ssl.conf
Red colored entries are to be modified as per your requirement
<IfModule mod_ssl.c> <VirtualHost _default_:443> ServerAdmin [email protected] ServerName web.itzgeek.com DocumentRoot /var/www/html ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined SSLEngine on SSLCipherSuite ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:EC$ SSLHonorCipherOrder on SSLOptions +StrictRequire SSLCertificateFile /etc/letsencrypt/live/web.itzgeek.com/cert.pem SSLCertificateKeyFile /etc/letsencrypt/live/web.itzgeek.com/privkey.pem SSLCertificateChainFile /etc/letsencrypt/live/web.itzgeek.com/chain.pem <FilesMatch "\.(cgi|shtml|phtml|php)$"> SSLOptions +StdEnvVars </FilesMatch> <Directory /usr/lib/cgi-bin> SSLOptions +StdEnvVars </Directory> </VirtualHost> </IfModule>
We will also configure HTTP to HTTPS redirection on Apache server so that the traffic comes to non-HTTPS site redirect to the HTTPS site.
### CentOS / RHEL ### vi /etc/httpd/conf.d/redirect.conf ### Ubuntu / Debian ### nano /etc/apache2/sites-enabled/redirect.conf
Use the below information.
<VirtualHost *:80>
ServerName web.itzgeek.com
RewriteEngine On
RewriteRule ^ https://%{SERVER_NAME}%{REQUEST_URI} [END,NE,R=permanent]
</VirtualHost>
Restart the Apache service.
### CentOS / RHEL ### service httpd restart ### Debian / Ubuntu ### a2enmod rewrite a2enmod ssl a2ensite default-ssl.conf service apache2 restart
Place a test index file on Document root.
echo "This is SSL site" > /var/www/html/index.html
Verify the Let’s Encrypt certificate by visiting HTTPS version of your website.
OR
You should get HTTPS version of your site now.
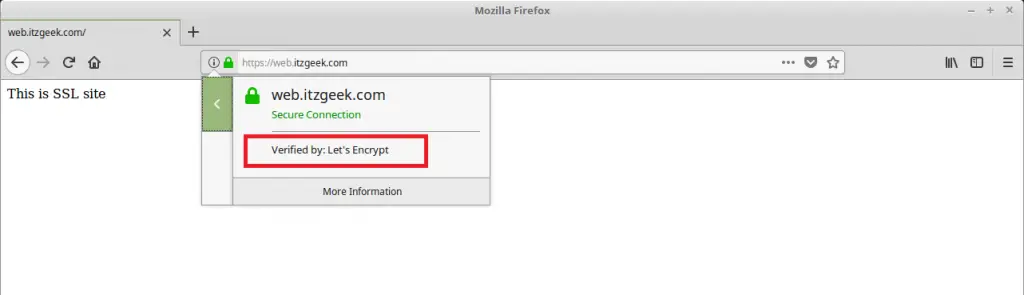
Verify SSL Certificate
Test your SSL certificate for any issues and its security ratings by going to the below URL.
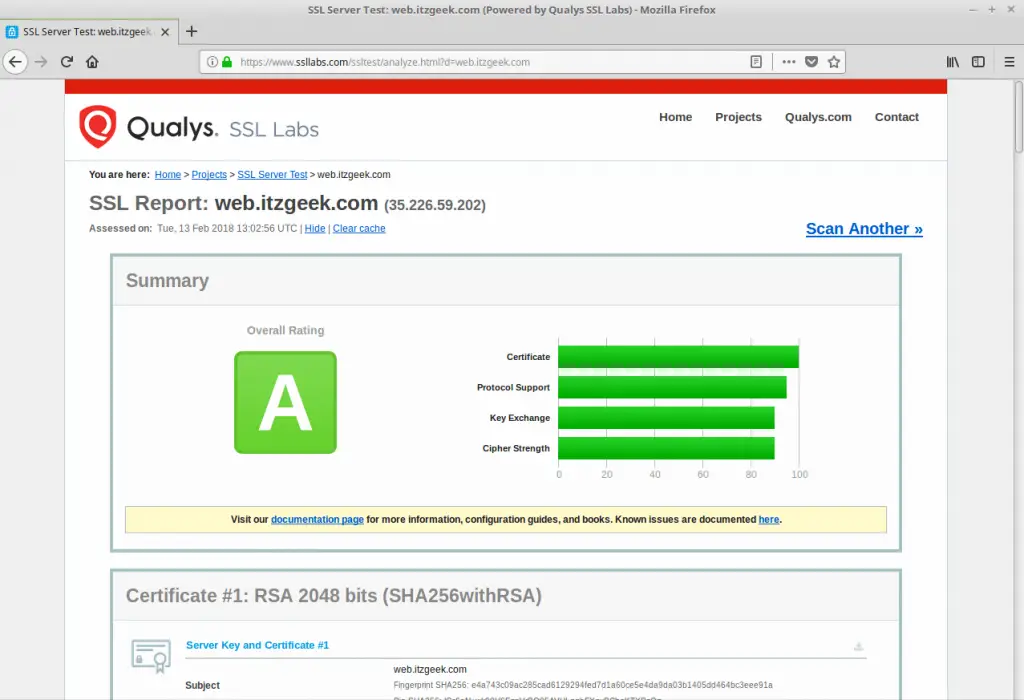
Certificate Renewal
Let’s Encrypt certificates have a less validity, about 90 days, and it is highly advisable to configure the cron (Linux Scheduler) job to renew your certificates before they expire.
Before you configure the cron job, run a below command to simulate automatic renewal of your certificate.
certbot renew --dry-run
Output:
Saving debug log to /var/log/letsencrypt/letsencrypt.log ------------------------------------------------------------------------------- Processing /etc/letsencrypt/renewal/web.itzgeek.com.conf ------------------------------------------------------------------------------- Cert not due for renewal, but simulating renewal for dry run Renewing an existing certificate Performing the following challenges: http-01 challenge for web.itzgeek.com Waiting for verification... Cleaning up challenges Generating key (2048 bits): /etc/letsencrypt/keys/0001_key-certbot.pem Creating CSR: /etc/letsencrypt/csr/0001_csr-certbot.pem ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates below have not been saved.) Congratulations, all renewals succeeded. The following certs have been renewed: /etc/letsencrypt/live/web.itzgeek.com/fullchain.pem (success) ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates above have not been saved.) IMPORTANT NOTES: - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal.
The above output confirms that the renewal is working properly. Now, configure a cron job for the below command.
certbot renew
Note: We recommend configuring the cron job to run twice per day.
That’s All.
